MuddyWater is an APT group that has been active throughout 2017, targeting victims in the Middle East with in-memory vectors leveraging on Powershell.
In October 2018, Kaspersky Lab has already published a good analysis report on the malwares by this APT group.
Here I am publishing my analysis report on recent malware by this APT group which targetted several parts of the Middle East.
Sample - 8899c0dac9f6bb73ce750ae7b3250dbd (Virustotal)
References :
https://www.vmray.com/analyses/c873532e009f/report/overview.html
https://twitter.com/360TIC/status/1081080752438009856
https://www.virustotal.com/#/file/c873532e009f2fc7d3b111636f3bbaa307465e5a99a7f4386bebff2ef8a37a20/detection

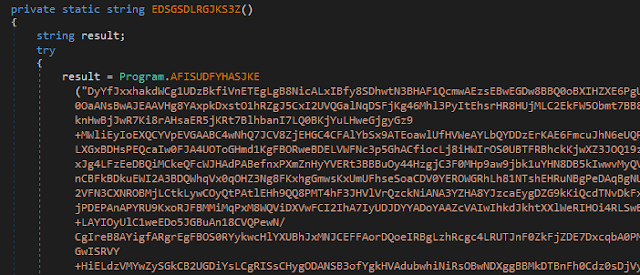
The document has obfuscated macro code which contains encrypted binary data. On execution, it decrypts the data and drops files and execute it.
The decryption function used in VBS macro is shown below.
With the help of this function, it decrypts lin(0) of the code shown in below image which is nothing but the header of a PE file.
The macro concatenate above lines and converts it in Ascii and stores it at "C:\users\public" with the name of "temp_rt_32.exe".
After that, it concatenates another code shown below and stores it at the same location with the name of "Data.zip"
Location - C:\Users\Public
After that, the document ShellExecute the temp_rt_32.exe and exit itself.
temp_rt_32.exe :
temp_rt_32.exe is a UPX packed Delphi file. On execution, it extracts the data.zip file at %PUBLIC% location and executes "GoogleUpdate.exe"
And then it imports UP.txt file to the registry which is nothing but the RUN entry of GoogleUpdate.exe with the name of DVRStudio and exit itself.
GoogleUpdate.exe :
GoogleUpdate.exe is a RAT which downloads another malware in the system or uploads user's files to command and control server.
First of all, it creates a path ""\\Windows\\Microsoft\\FrameWork4"" in %APPDATA%.
Then it creates a unique machine ID by Base64 of username and Volume serial number.
ID = base64_encode(username_volumeserialnumber)
After that, it checks the internet connectivity by resolving google.com. If it returns true, it will do the malicious activity otherwise it will wait for 5min.
If the internet is connected then it reads "C:\Users\Public\temp_gh_12.dat" which has following encoded data.
"NAAbYiYadQF4QQAAMXo2Oic7CT4nORx/N3oYKwReWSMEMwAuCGxlX3ZUYmEHEh4+Gz0RPxgVBi8QYBY/aWITJQQGImZ2Y1cLdncHIQ8iHywJMhAgHxgfJRx1GUlvEhl9HRIIUG1wclB9Zw8/AiwQPQYCDmMCOBxv"
The above function will Base64 decode the data of temp_gh_12.data, XOR the decoded data with the hardcoded key and then again Base64 decode the decrypted data.
Here the key is "UHIRER874893UIUOFUGHEWROUIRGH35"
so after decryption of temp_gh_12.dat file, it shows up a below URL.
hxxps://www.jsonstore.io/4de4d6d84d17638b3cd0eaf18857784aff27501be7d3dd89fad2b7ac2134f52e
The sample downloads the JSON file from the above URL and gets the URL of the CnC server.
Above jsonstore api has two CnC URLs. The sample will parse this URLs and proceed with the active one.
When it finds the active URL, It takes infected machine information, encode and encrypt it and stores it at %APPDATA%\\Windows\\Microsoft\\FrameWork4 with the name id_uniqueID (eg. id_dXTlbl9DRT).
The information is in below format.
MachineName_UserName_UserDomainName_OperatingSystem_DateTime_IPAddress_ServerURL
Each info is first encoded with Base64 and then XOR encrypted by hardcoded key.
The sample reads this info from the file and sends it to the CnC server at the below URL.
hxxp://shopcloths.ddns.net/users.php?tname=id_UniqueID&path=Users
The sample has Base64 encoded and XOR encrypted PowerShell script which is decrypted by the same encryption and encoded method describe above.
The decrypted PowerShell script looks like below.
The first function of the script gives all the usernames available in the system.
The second function will give all the environment variables present in the system path and all the services which are currently running in the system.
ipconfig /all - gives the network info of the system.
The sample runs this script and takes the output, encode and encrypt it with the same method described above and then stores it at %APPDATA%\\Windows\\Microsoft\\FrameWork4\\res_uniqueID.frk
After that, it reads the same file and send it to CnC server at below location and then deletes the file.
hxxp://shopcloths.ddns.net/users.php?tname=res_uniqueID.frk&path=Data
After all these initialization steps, control transfer to an infinite loop which takes care of all the action coming from server and act accordingly.
This loop first checks the internet connection by pinging to google.com then it checks server connectivity by sending follwing request to server and comparing output with the hardcoded value.
hxxp://shopcloths.ddns.net/users.php?root=random_chars
The output of this request should be "wYbaej5avYrFb" which is hardcoded in the sample.
After handshaking, it reads action command by sending a request to following server URL with the unique machine ID.
hxxp://shopcloths.ddns.net/users.php?readme=Data/uniqueID
Currently, there are only three commands are present in this version.
1. Download Filename URL: It downloads a file from URL and saves it as Filename at %APPDATA%\\Windows\\Microsoft\\FrameWork4
2. Upload FilePath: It uploads FilePath on the server at URL hxxp://shopcloths.ddns.net/users.php?tname=randomname.extension&path=Data
3. Powershell script: If the response of server is encoded and encrypted PowerShell script then it will run by the third function which is shown below.
IOCs :
Malicious word document : 8899c0dac9f6bb73ce750ae7b3250dbd
Zip dropper (temp_rt_32.exe) : 7C3DD70A4B1976481913E6B5A1FFBB77
Zip File (data.zip) : 5DB43101417247AE161C4425D0B96A70
RAT (GoogleUpdate.exe) : 6F44E57C81414355E3D0D0DAFDF1D80E
CnC URLs hosted on : hxxps://www.jsonstore.io/4de4d6d84d17638b3cd0eaf18857784aff27501be7d3dd89fad2b7ac2134f52e
CnC URL : hxxp://shopcloths.ddns.net/users.php?
CnC URL : hxxp://getgooogle.hopto.org/users.php?
Update - 13 Jan 2019
I have found some similar and recent malwares on Virustotal. All these samples have only one embedded PE file (GoogleUpdate.exe) which will be dropped in %TEMP%. In my case, this GoogleUpdate.exe was a Dotnet file embedded in the data.zip file and which was executed by temp_rt_32.exe. but here GoogleUpdate.exe is also a Dotnet file packed with enigma virtual box packer. Other than this, all the process and CnC servers are similar.
Here are the latest documents: (MD5)
d5f76641176d78477e14fde7ae073752
f589af2ae8f1ace804ef5745feeb6d5c
44284b5eb3b6da8c988924907478adbd
85b3f269251d805d3e2f78d37aeb1744
92816bd34efb6f8b7149d6c2c1545d6a
9f092a060381db4ed63d4e96da5c8d54
I have found some similar and recent malwares on Virustotal. All these samples have only one embedded PE file (GoogleUpdate.exe) which will be dropped in %TEMP%. In my case, this GoogleUpdate.exe was a Dotnet file embedded in the data.zip file and which was executed by temp_rt_32.exe. but here GoogleUpdate.exe is also a Dotnet file packed with enigma virtual box packer. Other than this, all the process and CnC servers are similar.
Here are the latest documents: (MD5)
d5f76641176d78477e14fde7ae073752
f589af2ae8f1ace804ef5745feeb6d5c
44284b5eb3b6da8c988924907478adbd
85b3f269251d805d3e2f78d37aeb1744
92816bd34efb6f8b7149d6c2c1545d6a
9f092a060381db4ed63d4e96da5c8d54